
Things to consider before installing Amazon Assistant
Amazon.com is one of those sites where you can find […]

Amazon.com is one of those sites where you can find […]

The infamous ransomware known as WannaCry has infected a quarter […]

Wallet ransomware virus has been attacking computer users for a […]
Ugetfix.com is one of eSolutions projects launched several years ago […]
Recently, security experts reported about a new tendency showing that […]
According to several users’ complaints that recently appeared on Reddit […]

Business can connect people for different challenges. However, when people […]
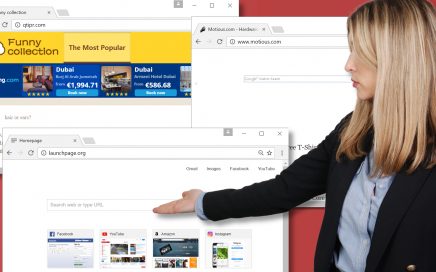
It is obvious that ransomware is one of the most […]
You might have already heard that the value of one […]
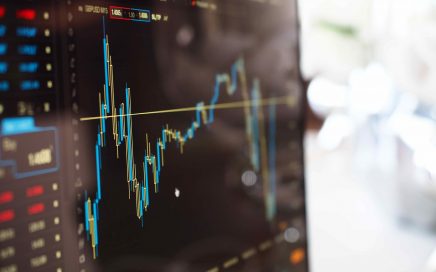
2016 was a busy year for security experts – computer […]
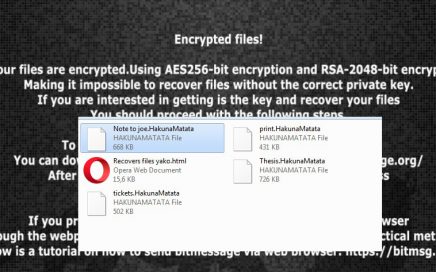
Hakuna Matata ransomware came out to light in the middle of January […]
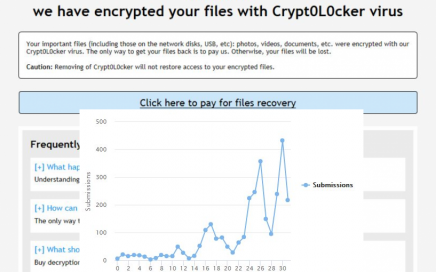
We must warn you about the growing danger of Crypt0l0cker ransomware. It […]
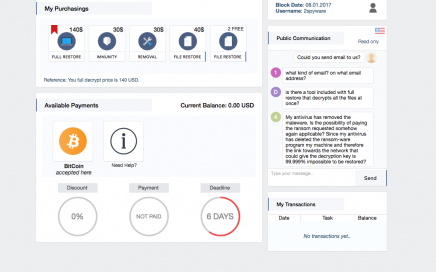
Spora ransomware was introduced by its developers in the beginning […]

Selecting the security software for computer’s protection has always been […]
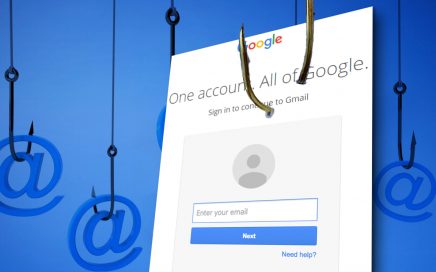
Cybercriminals are now targeting Gmail users, Wordfence reports. We have […]
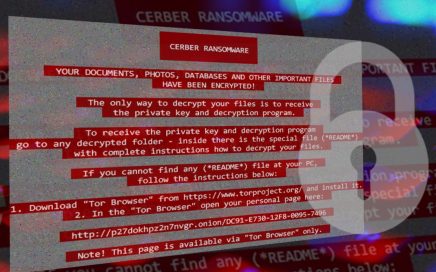
With a different design and improved distribution tactics, the new […]