
eSolutions warning: Sodinokibi ransomware keeps evolving and is considered a next big threat on the cryptovirus scene
Sodinokibi ransomware uses former Windows zero-day vulnerability and increases ransom […]
support blog for 2-spyware.com US English site.

Sodinokibi ransomware uses former Windows zero-day vulnerability and increases ransom […]
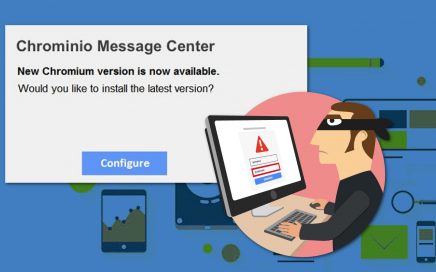
Chrominio virus spreading deceptive messages encouraging users to get unverified […]

ByteFence ditches its shady distribution method and stops changing browser’s […]
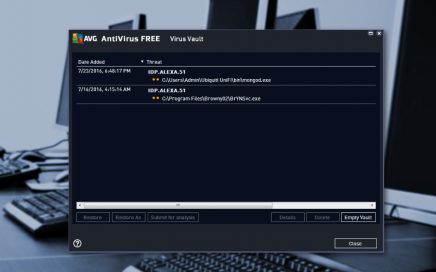
Idp.alexa.51 – malware detected by popular antivirus programs During the […]

Zeus Panda virus used SEO to attack users Security researchers […]

eSolutions warning: a new variant of Petya emerged! On the […]

Be aware of ransomware: your files are still in danger […]
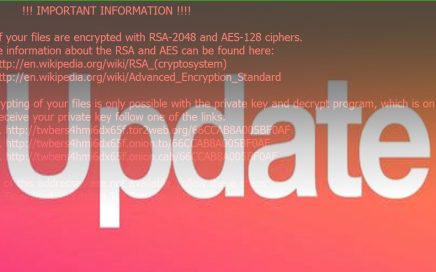
Locky remains to be a major issue in the cyber […]

Cerber or Locky – ever-evolving and ever-lasting cyber issues In […]

Researchers noticed an increased activity of adware programs Recently, cyber […]
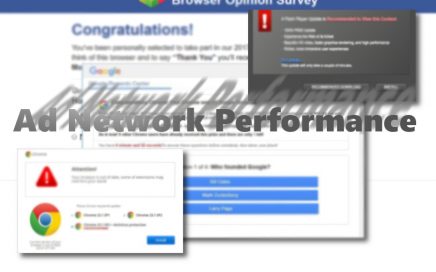
AdNetworkPerformance.com ads are looking for new victims If you have […]

Tech support scammers send fake alerts about Zeus infection Zeus […]
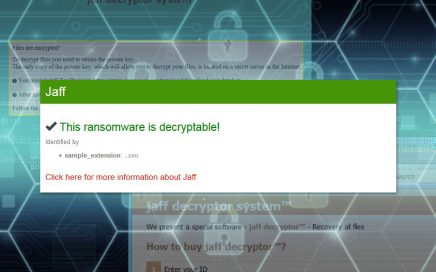
As Virus Activity blog reports, there’s no need to worry […]

Nearly a month has passed since the first reports about […]

Amazon.com is one of those sites where you can find […]

The infamous ransomware known as WannaCry has infected a quarter […]