
Authorities report millions in losses from COVID-19 scams
Millions of dollars stolen from citizens and business across USA […]

Millions of dollars stolen from citizens and business across USA […]

Sodinokibi ransomware uses former Windows zero-day vulnerability and increases ransom […]
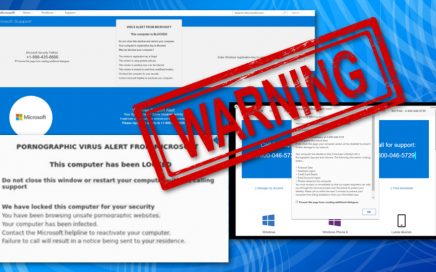
Warning: Fake virus alerts that lead to the money loss […]

Esolutions adds FirmusMedicus to the family of projects Our company […]

Mac malware is becoming more prevalent among cybercriminals While the […]

Because of phishing incidents, almost 90% of businesses have started […]

Fake alert about spyware scams people into calling tech support […]
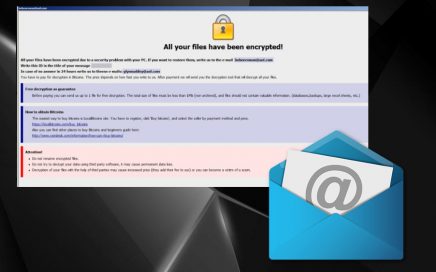
Dangerous ransomware releases fifteen versions in less than two years […]
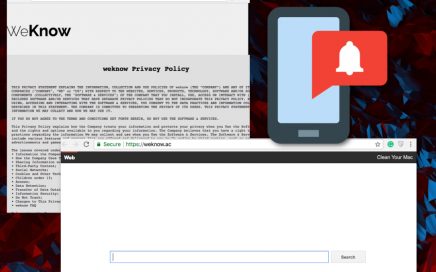
Browser hijacker redirects to questionable websites and delivers intrusive, suspicious […]
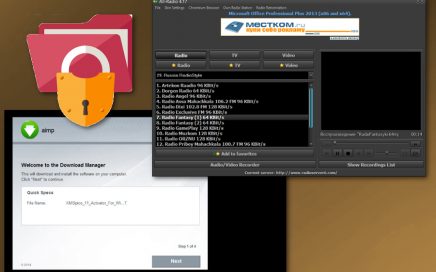
Experts noticed that the name of a legitimate video and […]
Dangerous ransomware is alive and attacking Ransomware is one of […]
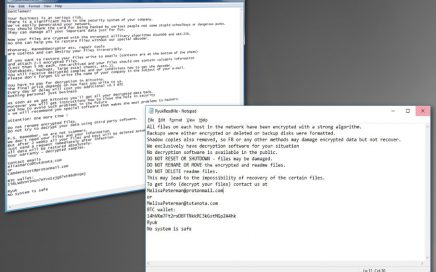
Detailed Ryuk ransomware attacks appear to be tailored to each […]
The new computer repair tool that improves the performance of […]
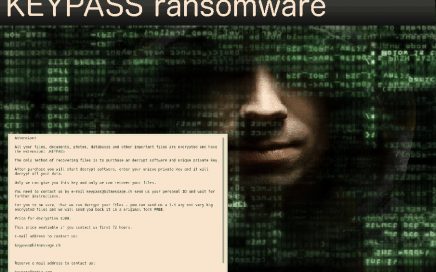
KEYPASS ransomware is creating more versions since the first attack […]
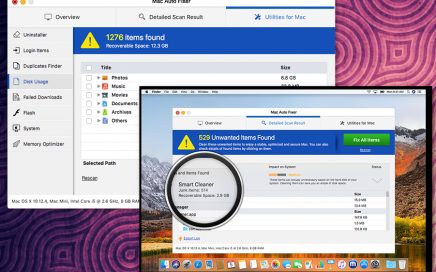
Another unwanted program that is promoted as a useful tool for […]
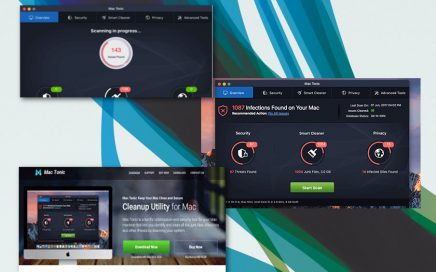
Another deceptive application promoted as an optimization tool Mac Tonic […]