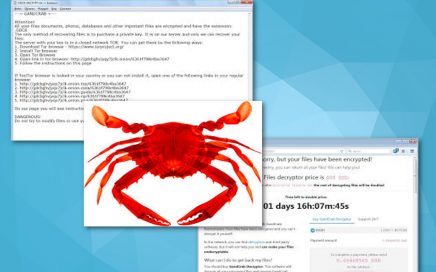
GandCrab v4 evolving: new version of a virus detected weekly
It was believed that GandCrab ransomware is a one-time thing, […]

It was believed that GandCrab ransomware is a one-time thing, […]
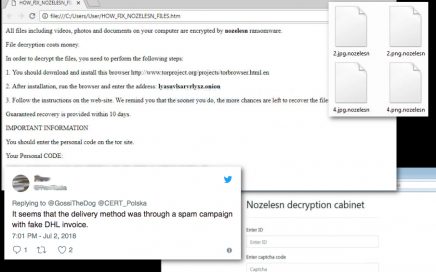
Nozelesn ransomware – a virus that uses DHL name in virus spreading […]
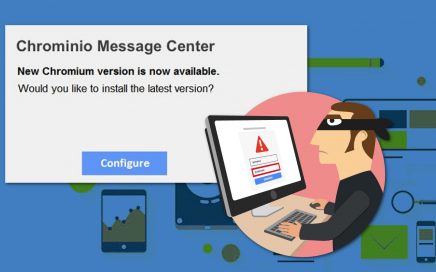
Chrominio virus spreading deceptive messages encouraging users to get unverified […]

ByteFence ditches its shady distribution method and stops changing browser’s […]
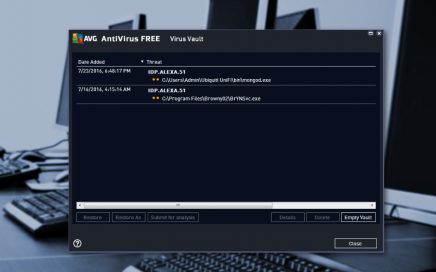
Idp.alexa.51 – malware detected by popular antivirus programs During the […]
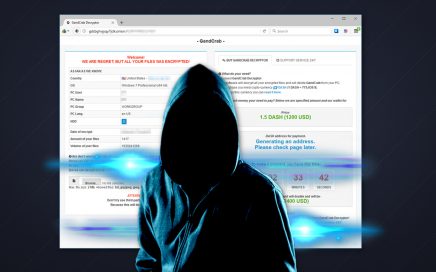
GandCrab ransomware is the first to accept DASH cryptocurrency GandCrab […]
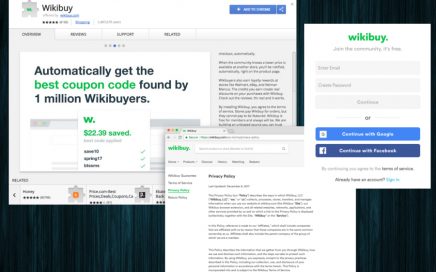
eSolutions: it is not worth downloading Wikibuy extension If you […]
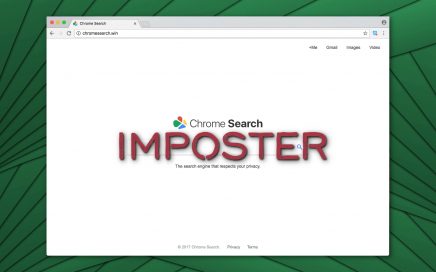
Chromesearch.win virus is nothing more than an impersonator of Google […]

The developers of Scarab ransomware employ Necurs botnet for distribution […]

Zeus Panda virus used SEO to attack users Security researchers […]

Matrix, Losers and Magniber ransomware on a rise in November […]

eSolutions warning: a new variant of Petya emerged! On the […]

Criminals use Chromium project to develop fake versions of Google […]

Be aware of ransomware: your files are still in danger […]

New details discovered about Yahoo data breach If you had […]

Miners might replace ransomware in the future Have you been […]