Dangerous ransomware releases fifteen versions in less than two years
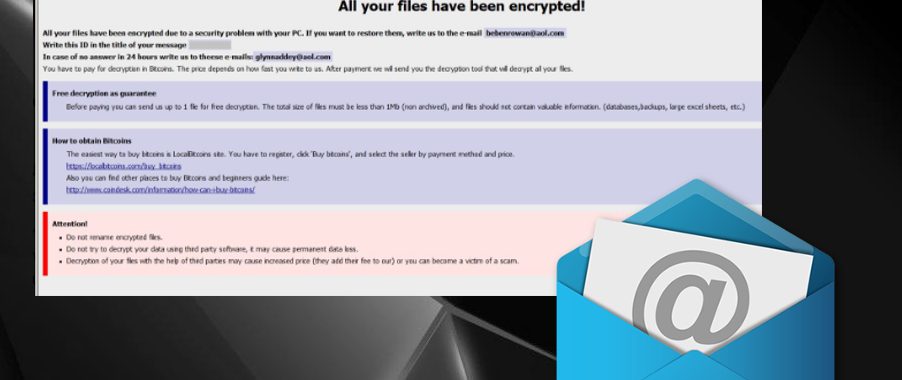
Esolutions have spotted two new versions of Dharma ransomware attacking people all over the world. These newly coded variants emerged less than a week apart. Bringing two new file extensions in the similar pattern as previous intruders, these crypto extortionists encrypt data using both RSA and AES encryption algorithms. This makes encoded files even more difficult to decrypt. However, we are not suggesting to contact these hackers because people behind threats like this are not trustworthy and the alleged decryption tool may not even exist.
The second week of September came with the news about Brrr ransomware that has .[[email protected]].brrr file extension added on encoded files. This pattern of an appendix is similar to other versions of the Dharma family. Less than a week after, Gamma ransomware was discovered with .id-.[[email protected]].gamma file extension as a marker for encrypted photos, videos, and documents. Another similar feature is two files for ransom note that has the same names since 2016: Info.hta and FILES ENCRYPTED.txt.
Same ransomware family has more than ten variants
The main ransomware family activity started with Dharma and the first attack in November 2016. Since then, there is a new version discovered every few months because CrySis/Dharma developers are not sleeping. Every new version has code slightly changed, so encryption is different and not so easily decryptable with previously developed decryption tools. Various cybersecurity experts have developed decryption tools for some versions, but since the code is changed with each release, it is not possible to use one decryptor for a few different versions.
There is as many different extensions, contact emails, and ransom notes as there are variants of ransomware. However, the content of the ransom message slightly changes while the main name of these files is not differing from the first one. Unfortunately, it looks that the hackers behind this cyber threat are not going to stop shortly.
Blocking Dharma ransomware before it is too late
Since this is a cyber threat, it comes to your computer in various ways. Most common is spam email attachments used to spread malware that installs ransomware or file attachments with the direct malicious script. Because of this reason, various antivirus programs identify the same threat in different names:
- TR/Kryptik.whocg
- Trojan.IGENERIC
- Trojan.Win32.Krypt
- Trojan.Encoder.ar
- Ransom.Crysis
- Trojan.Gen.2
- TR/Dropper.Gen
- Ransom.Crysis.Generic
This fact that antivirus and anti-malware tools can detect this virus means that the best way to remove this virus from your device is the same malware-fighting programs. Using anti-malware tools can be beneficial for various parts of the system because the full system scan indicates what intruders you have on the computer, which software needs updates and what system vulnerabilities can be fixed. This automatic ransomware removal help improve the overall performance of your computer and avoid more significant damage if you do it as soon as you notice encrypted files.