Detailed Ryuk ransomware attacks appear to be tailored to each individual business separately
The hacker group behind this highly targeted ransomware attack made over $640 000. Ryuku ransomware exists and works only for two weeks but the profit from 10 or even fewer victims make these people rich. This virus attacks large businesses and the demanded ransom amount gets to 50 BTC. This depends on the company and the time a victim spends before paying. Ransom differs from 15 to 50 BTC but each day ads a half of Bitcoin to the price. If a victim waits longer than two weeks there is no opportunity to get those files back.
This ransomware needs to gain admin access to the system to run wanted processes on the computer. This is why there is a lot of planning involved and it is believed that the team behind this malware are experienced in these type of targeted attacks. This attack involves extensive network mapping, stealing of credentials and data encrypting functions. Even ransom message is more detailed when the attack is geared toward a big company.
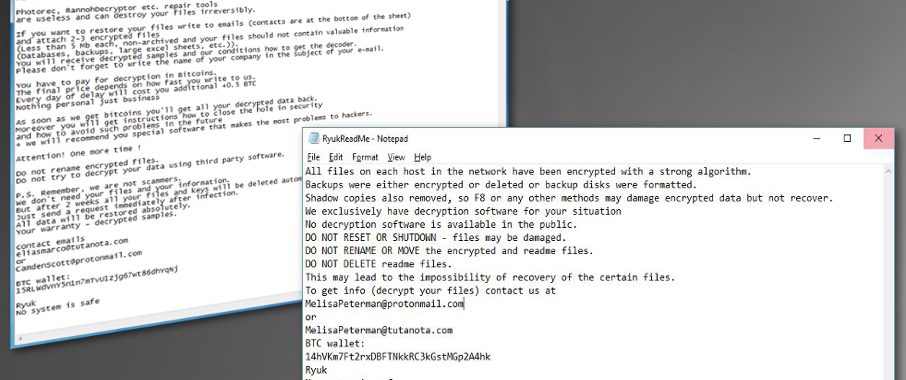
The virus is showing different ransom notes for companies and PC users
Ryuk ransomware is a virus that performs targeted attacks and based on financial profiting, it gears more towards large companies. Because corporates are more likely to be willing to pay hefty amounts to get back to working as smoothly as before. It is known that one company already paid more than $300 000 in bitcoin, for the developers of this ransomware. It is not surprising that only two weeks of these targeted attacks made the people behind this malware $600k richer already.
According to reports from cybersecurity researchers this ransomware displays different ransom notes for the different victim. If Ryuk attacks a large company it displays a lengthy ransom message that is written somewhat polite. It has more information about the attacks and virus developer suggest to pay the ransom because they can include tips and tricks on system vulnerability fixing and also a software that supposedly makes a difficult time for other hackers to get on the system. Also, the average people ransom note has nothing about test decryption or encryption methods.
Functionality similar to a North Korea-based hacker group
Infamous Lazarus hacker group had been spreading similar malware called Hermes ransomware. This virus had a few versions already. Many researchers pointed out the similarities between Ryuk and this infection. It is either the same team using the same source code or different team using the code of a well-known malware. Since it is fairly difficult that two different teams use the same code and have other similarities it is believed that Lazarus is behind Ryuk also.
This targeted attack infiltrates the system using those system vulnerabilities developers mention in the bigger ransom note. But there is a possibility that ransomware gets on the system by abusing poorly protected RDP configurations. There is also pishing spam email campaigns that are commonly used to spread malware around the world. All of these methods are silent and dangerous.