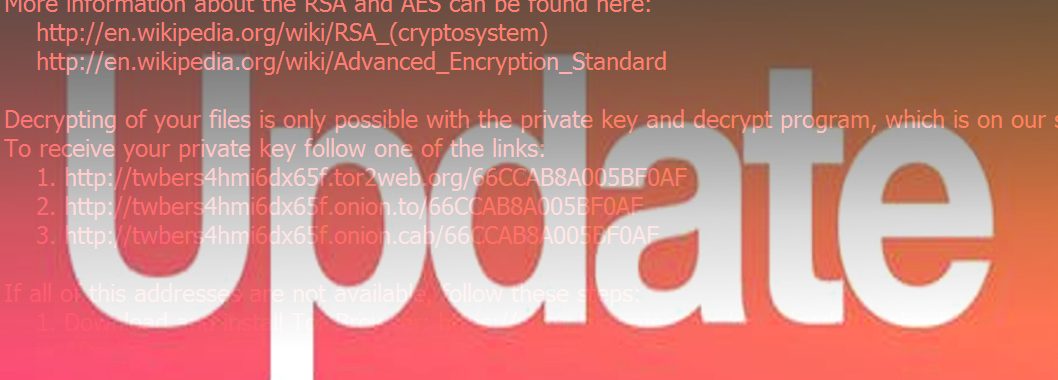
Locky remains to be a major issue in the cyber space
Perhaps Locky developers ran out of crafty ideas as they ceased making up intriguing names for their malware. After Diablo6 and Lukitus versions were released, the crooks launched a supposedly new version with a brand new name – Ykcol – which is Locky backward.
Any new features?
The latest version does not manifest any exceptional prowess. Besides the alternations in the name, the source code does not seem to have been changed drastically. Nonetheless, there are slight amendments in the distribution campaign.
The menace continues relying on the Necurs botnet which delivers thousands of spam emails worldwide. Since the introduction of Diablo6 and Lukitus extensions, a change in the employed folder type was spotted as well.
Earlier versions of ransomware tended to hide in a .rar folder, but latest editions, including Ykcol, are placed in .7z folder. It contains a VBS script which activates the execution of the file-encrypting threat.
Locky developers retained the habit of disguising the malware in invoice emails. Previous editions were delivered along with a brief message “Files attached. Thanks”. Ykcol tends to fish for gullible users with “Could you please let me know the status of the attached invoice? I appreciate your help!” messages. An alternative sample of the menace tries to persuade potential victims to launch the virus by disguising under the name of Herbalife Nutrition company, which is the nutrition and weight management company located in the US.
From invoices to fake verification emails
While the attention is concentrated on Ykcol ransomware, Lukitus and Diablo6 crypto-viruses should not be ignored as well. Recent analysis reveals that the racketeers disguise the malware under fake Dropbox account verification emails.
In addition, company employees should be especially vigilant about Locky. There have been versions detected which include counterfeited scanned .png images. They are called as scanned printer images.
The problem is that Locky targets company servers. Consequently, it can easily foist such message. Unsuspecting users, thinking that the email was sent by a colleague, might open the corrupted version only to find out Ykcol or Lukitus encrypting their files afterward.
However, though the developers of this menace seem to use conservatives techniques, Locky still remains undecryptable.
Considering prevention means, attentiveness and cyber security are the key factors in warding off Locky:
- install system updates once they are published
- update security tools
- use a couple of different type anti-malware apps
- double-check the sender of a received suspicious email