eSolutions warning: a new variant of Petya emerged!
On the 24th of October, the new version of Petya ransomware was reported to attack Russian and Ukrainian organizations. Petya is known for attacking Ukraine companies and public sector. However, this time the recently discovered Bad Rabbit ransomware hit Russia in a harder way.
According to the latest information, Bad Rabbit virus was reported to attack Kiev’s Metro and Odessa International Airport. Even though there’s still not a lot of information about the damaged caused to these infrastructure’s systems, the attack is warning sign to all organizations and companies to make sure that their systems and networks are protected.
Additionally, reminding employees security tips is also recommended. The current version of Petya virus spreads as fake Adobe Flash update. Thus, inexperienced users can be easily tricked into downloading a malicious file and causing serious problems to the whole computer network.
However, security researchers did not take long to find a vaccine to prevent ransomware infiltration. Though, basic security tips are also recommended to follow.
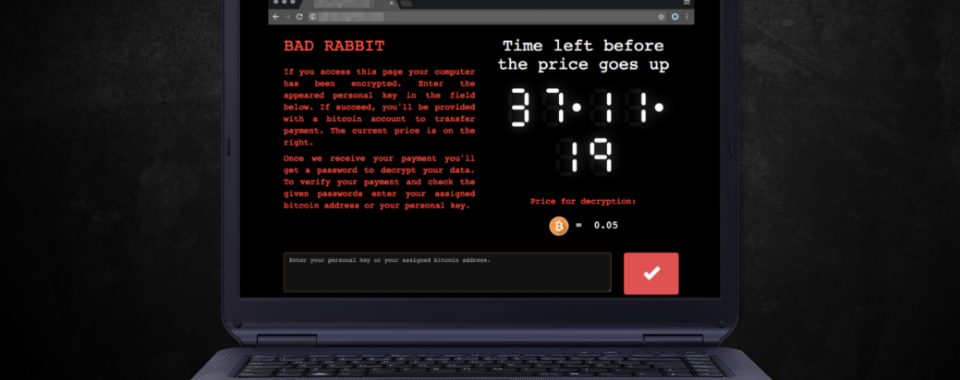
Bad Rabbit malware masquerades as Flash update
Drive-by downloads are one of the distribution methods used for spreading Bad Rabbit ransomware virus. The fake Flash update is injected into compromised websites. If users end up on a malicious site, they receive a pop up asking to install the latest update. Once they hit “Install” button, the malicious executable is dropped to the Win32/Filecoder.D folder. Then the install_flash_player.exe file is executed, malware starts data encryption procedure.
However, malware might also exploit a vulnerability in Windows Server Message Block (SMB). At first, it was thought that malware uses EthernalBlue vulnerability. However, latest analysis data says that it’s not true. Malware just scans the internal network and looks for open SMB shares. If it finds, it might affect the whole network.
Protecting computers and networks from ransomware
Bad Rabbit ransomware might cause extreme damage to your company or paralyze important city infrastructures, such as public transportation. However, home computer users should be aware of security tips too.
After the infiltration, malware immediately locks files with a combination of RSA-2048 and AES-128-CBC encryption ciphers and makes them unable to open due to .encrypted file extension. In order to recover files, victims are asked to pay 0.05 Bitcoin. However, the size of the ransom might increase.
Security researchers discovered a vaccine that helps to protect devices from the latest version of the Petya ransomware:
- Create infpub.dat and cscc.dat files in c:\windows directory by running cmd.exe as an administrator and entering these commands:
echo “” > c:\windows\cscc.dat&&echo “” > c:\windows\infpub.dat - Right-click on each of the newly created files and select Properties.
- Access Security tab in the appeared Properties window.
- Click Advanced option.
- In the newly appeared window click “Change Permissions…” button.
- Uncheck “Include inheritable permissions from this object’s parents” box (Windows 10 users have to choose “disable inheritance button” and then select “Remove all inherited permissions from this object”).
- You will receive a Windows Security pop up. Click Remove button.
Additionally, security experts do not recommend paying the ransom and advise to take precautions in order to avoid losing important data loss:
- Enable automatic Adobe Flash Player updates. In this way, you or your employees will not be tricked into installing bogus update from the pop-up window.
- Patch the Windows SMB protocol. Also, make sure that your operating system has all necessary security fixes. Install them as soon as they are offered by Microsoft.
- Install available software updates. Enabling automatic software updates help to avoid misleading alerts. However, if you prefer monitoring updates, you should be careful and do not forget to install them regularly.
- Do not open suspicious email attachments. Often ransomware-type viruses spread via malicious spam emails that include an infected attachment. Before opening any attached safely looking files, please check the information about the sender and provided an issue to make sure that it’s actually safe to open.
- Backup data and update it regularly. Having extra copies of the most important files reduces the damage in case of ransomware attack.
- Strengthen computer’s protection by installing reputable antivirus.